EN | Alert-box Message Content Manipulation based Base64
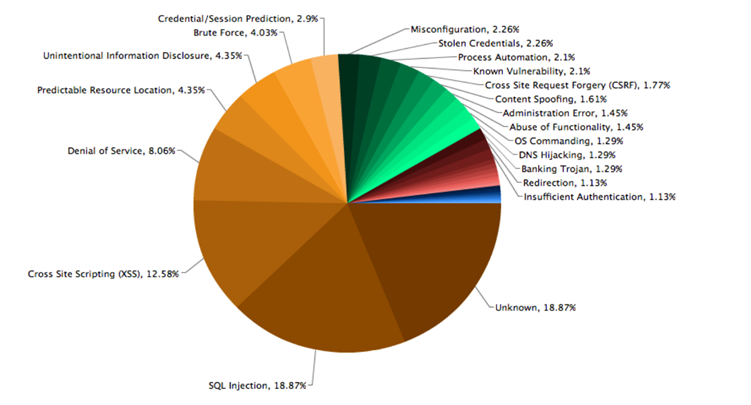
In July of this year, I found a Content Spoofing vulnerability in a Bitcoin Exchange company. The system was very simple, an encrypted text in a GET parameter was decrypted and reflected on the homepage in an alertbox. I know it’s very simple and its impact is very low. In my philosophy, every finding is worth reporting. Then, I reported this weakness and the company rewarded me with a $$$ bounty.
Recon
I was doing research on page of the website that do not require authentication, and I started researching the login page. While trying to login with some default credentials, I saw it execute “wrong username or password” warning on an GET parameter named “?e=”. I saw the parameter’s value is encrypted with Base64 and tried printing something else. The website did not fail and reflected what I wrote on the screen as a warning.
Mechanism
I placed the text in the picture below, which I encrypted with Base64, into the parameter. The system also executed this message.
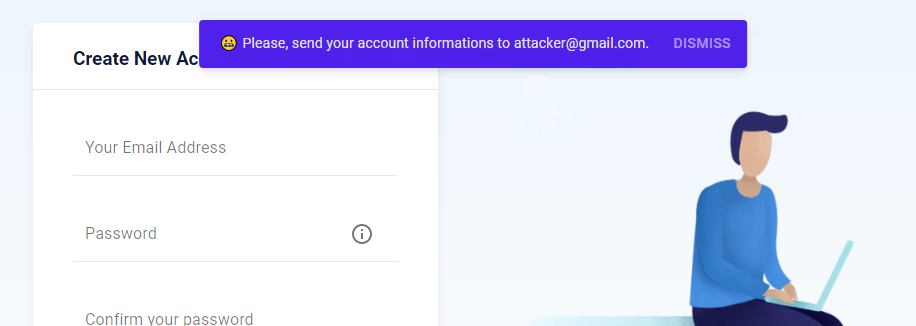
Weakness is weakness…
I know that this vulnerability is simply and very low impact. Personally, I am careful to report every findings I find.
The end :
17 June 2020 - Report sent
18 June 2020 - Confirmed
27 June 2020 - I was awarded a $100 bounty
